CIRCL » Botfree.lu - Luxembourg anti-botnet support - ACDC Luxembourg support center
Infected systems are often part of a botnet which can be controlled remotely by attackers to perform criminal activities like attacking other computers, send malicious emails or perform denial-of-service attack.
My PC is infected and I’m looking for supportIf you have a strong suspicion that your machine is infected and you are looking for support to reinstall the system, you can check the PC-doctor list to find a SME to support you.
I received a malicious or suspicious linkPhishing link can be directly tested and reported via the CIRCL urlabuse interface.
I have a security incident in my companyIf you have a security incident in your company, you can report it to CIRCL.



 Your new post is loading...
Your new post is loading...



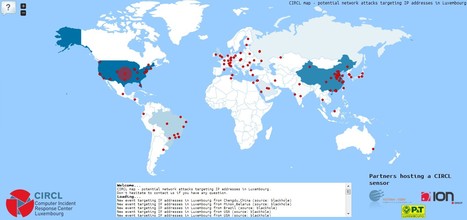




Botfree.lu - Luxembourg anti-botnet support - ACDC Luxembourg support centerInfected systems are often part of a botnet which can be controlled remotely by attackers to perform criminal activities like attacking other computers, send malicious emails or perform denial-of-service attack.
My PC is infected and I’m looking for supportIf you have a strong suspicion that your machine is infected and you are looking for support to reinstall the system, you can check the PC-doctor list to find a SME to support you.
I received a malicious or suspicious linkPhishing link can be directly tested and reported via the CIRCL urlabuse interface.
I have a security incident in my companyIf you have a security incident in your company, you can report it to CIRCL.