Brian KREBS @briankrebs (Twitter)
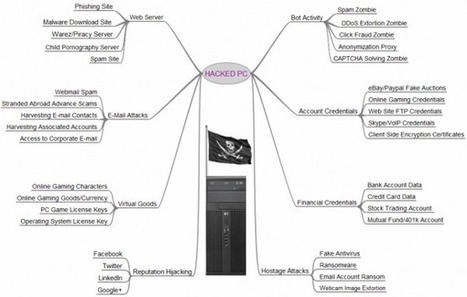
A few years back, when I was a reporter at The Washington Post, I put together a chart listing the various ways that miscreants can monetize hacked PCs. The project was designed to explain simply and visually to the sort of computer user who can’t begin to fathom why miscreants would want to hack into his PC. “I don’t bank online, I don’t store sensitive information on my machine! I only use it to check email. What could hackers possibly want with this hunk of junk?,” are all common refrains from this type of user.
I recently updated the graphic (below) to include some of the increasingly prevalent malicious uses for hacked PCs, including hostage attacks — such as ransomware — and reputation hijacking on social networking forums.
Learn more:
https://gustmees.wordpress.com/2013/10/25/cyber-security-blogs-to-follow/
https://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
https://gustmees.wordpress.com/2012/11/29/cyber-hygiene-ict-hygiene-for-population-education-and-business/



 Your new post is loading...
Your new post is loading...




Learn more / En savoir plus / Mehr erfahren:
https://gustmees.wordpress.com/2012/11/05/naivety-in-the-digital-age/