 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
The Hive ransomware gang now also encrypts Linux and FreeBSD using new malware variants specifically developed to target these platforms.
However, as Slovak internet security firm ESET discovered, Hive's new encryptors are still in development and still lack functionality.
The Linux variant also proved to be quite buggy during ESET's analysis, with the encryption completely failing when the malware was executed with an explicit path.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Sophos’s Managed Threat Response (MTR) team has warned the industry of a dangerous new ransomware trick – encrypting data only after rebooting Windows PCs into ‘safe mode’.
Deployed recently by the Russian-developed ‘Snatch’ ransomware – named after the 2000 movie of the same name – it’s effective against much endpoint security software, which often doesn’t load when safe mode is in operation.
That’s despite the fact that in real-world attacks analysed by MTR, Snatch starts out like many other ransomware campaigns currently targeting business networks.
The attackers look for weakly secured Remote Desktop (RDP) ports to force their way into Azure servers, a foothold they use to move sideways to Windows domains controllers, often spending weeks gathering reconnaissance.
In one network attack, the attackers the installed the ransomware on around 200 machines using command and control (C2) after utilising a grab-bag of legitimate tools (Process Hacker, IObit Uninstaller, PowerTool, PsExec, Advanced Port Scanner) plus some of their own.
The same software profile was detected in other attacks in the US, Canada and several European countries, which also exploited exposed RDP. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Security vulnerabilities in popular internet-connected digital cameras could allow hackers to infect them with ransomware, rendering the devices useless, or deploy other forms of malware which could potentially turn a camera into a gateway for infecting larger networks.
Digital cameras use Picture Transfer Protocol (PTP), a standard protocol to transfer digital files. Researchers at cybersecurity company Check Point Software found that it was possible to exploit vulnerabilities in the protocol to infect a camera with ransomware, presenting their findings at the Defcon security conference in Las Vegas.
The researchers looked at the Canon EOS 80D because it has both USB and Wi-Fi connectivity, as well as an extensive modding community which provides open source software for the camera. But while this particular model was chosen for the experiment, researchers warn that any internet-connected digital camera could be vulnerable to the attacks.
"As PTP is widely used by all digital camera vendors, we do believe that similar vulnerabilities will affect other vendors as well," Eyal Itkin, security researcher at Check Point, told ZDNet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
CERT-Bund, das Notfallteam des BSI, warnt aktuell vor einer besonders perfiden Ransomware-Variante: Das an ein vermeintliches Bewerbungsschreiben angehängte Zip-Archiv enthält mitnichten den Lebenslauf als Word-Dokument, sondern eine Windows-Link-Datei. Diese startet beim Klick die Powershell in Windows, um die eigentliche Malware von einem Server nachzuladen. Die Bewerbungsmail verwendet verschiedene Namen und Absenderdomains, sodass sich die Malware daran nicht zuverlässig erkennen lässt. Sprachlich gibt die Mail kaum Anlass zum Argwohn. Soweit nichts Neues.
Aber wer den GermanWiper getauften Trojaner arglos aktiviert, der verliert Daten dauerhaft: Statt sie aufwendig zu verschlüsseln, überschreibt die Malware Dateien mit Nullen und ändert die Dateiendung, bevor sie die Lösegeldforderung anzeigt. Der sollte man auf gar keinen Fall nachkommen. Der einzige Schlüssel zum Wiederherstellen der Daten ist das eigene Backup, nachdem man den PC gesäubert hat. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE https://www.scoop.it/topic/securite-pc-et-internet/?&tag=GermanWiper

|
Scooped by
Gust MEES
|
La mise à jour à mi-année s’intéresse aux tendances observées entre janvier et juin 2018. Parmi les enseignements les plus significatifs, le remplacement des ransomwares comme outil de cybercriminalité de choix par les logiciels de minage de cryptomonnaie. Au cours des six derniers mois de 2017, les ransomwares représentaient 32% des attaques, alors que les attaques de minage de cryptomonnaie ne représentaient, elles, que 7%. Au premier semestre 2018, les chiffres se sont presque exactement inversés : les attaques de minage de cryptomonnaie représentent 32% des attaques, contre 8% pour les ransomwares. «Ces dernières années, les ransomwares étaient pour les cybercriminels le moyen par excellence de gagner de l’argent rapidement », déclare Karl Buffin, Directeur des Ventes Europe du Sud chez Skybox Security. « Ce genre de programmes ne nécessitent pas d’exfiltrer des données, il suffit d’utiliser le cryptage / chiffrement pour retenir en otage les données et une note explicative indiquant à la victime comment elle peut payer la rançon. Dans le cas du minage de cryptomonnaie, les criminels peuvent aller directement à la source et miner des cryptomonnaies eux-mêmes. Il n’est plus question de savoir s’ils seront payés ou pas. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Crypto+Mining https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
Opfer des Erpresser-Trojaners LockCrypt können aufatmen. Bitdefender ist es gelungen, eine der Ransomware-Varianten zu knacken. Das Tool steht ab sofort zum kostenlosen Download bereit.
Seit Mitte des vergangenes Jahres treibt die Ransomware LockCrypt ihr Unwesen. Die Malware schleicht sich auf fremden Rechnern ein, verschlüsselt dort wichtige Dateien und Dokumente und verlangt anschließend ein Lösegeld. Nach Angaben des Sicherheitsanbieters Bitdefender konzentrieren sich die Urheber von LockCrypt dabei weniger auf Privatanwender, sondern vor allem auf Unternehmen als Ziel. Zur Verbreitung nutzen sie meist Lücken im RDP-Protokoll (Remote Desktop Protocol).
Auch der Antiviren-Hersteller Eset hat sich immer wieder mit LockCrypt beschäftigt. Nach seinen Erkenntnissen verlangt der Erpresser-Trojaner in der Regel zwischen einem halben und einem ganzen Bitcoin für eine Wiederherstellung der verschlüsselten Daten und pro in einem Unternehmen betroffenem Server. Bei den in den vergangenen Monaten teilweise sehr hohen Bitcoin-Preisen kommen so schnell hohe Summen zusammen, die anfallen, wenn eine Wiederherstellung angestrebt wird. Laut Eset hat ein Unternehmen rund 19.000 US-Dollar gezahlt, um wieder an die Daten auf drei verseuchten Maschinen zu kommen.
Kostenloses Entschlüsselungs-Tool
Bitdefender stellt nun ein kostenloses Decryption-Tool zum Download bereit, mit dem sich zumindest bei einer LockCrypt-Variante die verschlüsselten Daten wiederherstellen lassen sollen. Nach Angaben des Anbieters funktioniert das Tool bei der LockCrypt-Version, die mit der Dateiendung „.1btc“ arbeitet. Andere Varianten wie „.lock“, „.2018“ und „.mich“ seien zwar ebenfalls entschlüsselbar, aber noch nicht in dem Tool enthalten. Opfer der LockCrypt-Variante, die die Dateiendung „.bi_d“ erzeugt, müssen ebenfalls weiter auf ein Entschlüsselungswerkzeug warten, da diese Version bislang noch nicht geknackt werden konnte.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/ict-security-tools/?&tag=Ransomware https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
Geleistete Lösegeldzahlungen sind nur die Spitze des Eisbergs und nehmen sich im Vergleich zu den übrigen (Folge-)Kosten einer Infektion eher gering aus. Die eigentlichen Schadenssummen umfassen auch andere Kosten:
Datenverlust
Ausfallzeiten
Ersatz / Neuaufsetzen von Infrastruktur
Produktivität
Kosten für IT-Forensik
Reputationsschäden
Leib und Leben - gerade in Fällen, in denen Krankenhäuser und Pflegeeinrichtungen betroffen sind.
Nach einer Studie von CyberSecurity Ventures, einem der weltweit führenden Forschungsunternehmen der Internetwirtschaft, wird sich die gesamte weltweite Schadenssumme für das Jahr 2017 schätzungsweise um oder über fünf Millarden Dollar bewegen. Das bedeutet einen Anstieg um das fünffache der Schadenssumme von 2016. Experten prognostizieren hier einen weiteren Anstieg bis auf das 15-fache innerhalb der kommenden zwei Jahre: Um 2019 herum könnten es Schäden in Höhe von über 11.5 Milliarden Dollar sein.
Werfen wir einen Blick auf die prominentesten Vertreter der Gattung Ransomware und darauf, wie solche astronomischen Schadenssummen zustande kommen. Die nachfolgende Tabelle enthält Hinweise auf ein bestimmtes Verhaltensmuster, nach dem sich Malware-Autoren zunehmen auf Wirtschaftszweige kontentrieren, in denen die Absicherung wichtiger Kundendaten einen hohen Stellenwert hat.
Die Tatsache, dass Lösegelder gezahlt werden und dass hier massive Imageschäden angerichtet werden, unterstreicht, dass diese Strategie Wirkung zeigt. Petna bildet hier eine Ausnahme, da dieser Schädling nie dazu gefdacht war, Profit zu generieren. Stattdessen war Petnas Ziel, betroffene Betriebe lahmzulegen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
The Feds have disrupted the prolific Hive ransomware gang, saving victims from a collective $130 million in ransom demands. But it remains to be seen how much of a blow the effort will be to the overall ransomware landscape.
The group's operations have been buzzing with activity for months, racking up more than 1,500 victims in 80-plus countries around the world since it appeared in June 2021, according to an announcement from the US Justice Department. The gang has been operating with a ransomware-as-a-service (RaaS) model, engaging in data theft and double extortion, and delivering its venom indiscriminately to school districts, financial firms, critical infrastructure, and others. At least one affiliate has become a bit of a hospital specialist, disrupting patient care in some attacks.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Cyber criminals using a new form of ransomware are going after healthcare and technology companies across Europe, the US and Canada in what researchers describe as 'carefully chosen' attacks.
Named Zeppelin, the ransomware appears to be based on another family of network-encrypting malware – VegaLocker – but has been built upon and improved to such an extent that the security analysts at BlackBerry Cylance who discovered it have classed it as a new form of ransomware.
Analysis of the code reveals that Zeppelin was first compiled in early November this year, but in the space of a month alone it has been discovered targeting networks of tech and healthcare companies across Europe and North America. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
Ramsomware continues to be one of the biggest menaces on the internet. Clicking on the wrong link could be enough to set off a sequence of events that ends with all your data being encrypted by crooks, who will only unlock it in return for a hefty ransom -- usually in bitcoin or another hard-to-trace cryptocurrency.
One of the nastiest types of ransomware has just come back to life
How Bitcoin helped fuel an explosion in ransomware attacks
How Bitcoin helped fuel an explosion in ransomware attacks
Ransomware-as-a-service allows wannabe hackers to cash-in on cyber extortion
Now ransomware is taking aim at business networks
Criminal ransomware gangs are well financed (thanks to all those bitcoin ransoms) and employ increasingly sophisticated tactics. Only low-level crooks are interested in encrypting PCs one-by-one: the big gangs seek backdoors into corporate networks and then explore until they are ready to cause maximum chaos (and a big payday) by encrypting as many devices as possible in one go.
It's not just criminal gangs that have noticed the power of ransomware: state-backed hacking groups have also used ransomware to create both chaos and profit for their backers.
What we're seeing is an arms race between the crooks looking for new ways to compromise systems and businesses trying to plug every gap in their defences. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
Thousands of web servers have been infected and had their files encrypted by a new strain of ransomware named Lilocked (or Lilu).
Infections have been happening since mid-July, and have intensified in the past two weeks, ZDNet has learned.
Based on current evidence, the Lilocked ransomware appears to target Linux-based systems only.
First reports date to mid-July, after some victims uploaded the Lilocked ransom note/demand on ID Ransomware, a website for identifying the name of the ransomware that infected a victim's system. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux https://www.scoop.it/topic/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
For the past week, a new ransomware strain has been wreaking havoc across Germany. Named GermanWiper, this ransomware doesn't encrypt files but instead it rewrites their content with zeroes, permanently destroying users' data.
As a result, any users who get infected by this ransomware should be aware that paying the ransom demand will not help them recover their files.
For now, the only good news is that this ransomware appears to be limited to spreading in German-speaking countries only, and with a focus on Germany primarily.
PRETTY BIG DISTRIBUTION CAMPAIGN
First signs of GermanWiper were reported earlier this week when victims started asking for help on the Bleeping Computer forums, a popular place where internet users congregate to get advice in dealing with ransomware infections. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE https://www.scoop.it/topic/securite-pc-et-internet/?&tag=GermanWiper

|
Scooped by
Gust MEES
|
Louisiana Governor John Bel Edwards has activated a state-wide state of emergency in response to a wave of ransomware infections that have hit multple school districts.
The ransomware infections took place this week and have impacted the school districts of three North Louisiana parishes -- Sabine, Morehouse, and Ouachita.
IT networks are down at all three school districts, and files have been encrypted and are inaccessible, local media outlets are reporting. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
In den ersten beiden Artikeln unserer Reihe zur Malware-Entfernung haben wir uns bereits damit befasst, wie Sie unbekannte Malware sowie potenziell unerwünschte Programme (PUPs) erkennen und entfernen können. Heute werden wir uns mit einer Malware befassen, die in den vergangenen Jahren einen regelrechten Boom erlebt hat: Ransomware. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
Researchers found they were able to infect robots with ransomware; in the real world such attacks could be highly damaging to businesses if robotic security isn't addressed.
Ransomware has been a headache for PC and smartphone users but in the future it could be robots that stop working unless a ransom is paid.
Researchers at security company IOActive have shown how they managed to hack the NAO robot made by Softbank and infect one with custom-built ransomware. The researchers said the same attack would work on the Pepper robot too.
After the infection, the robot is shown insulting its audience and demanding to be 'fed' bitcoin cryptocurrency in order to restore systems back to normal.
While a tiny robot making threats might initially seem amusing - if a little creepy - the proof-of-concept attack demonstrates the risks associated with a lack of security in robots and how organisations which employ robots could suddenly see parts of their business grind to a halt should they become a victim of ransomware.
"In order to get a business owner to pay a ransom to a hacker, you could make robots stop working. And because the robots are directly tied to production and services, when they stop working they'll cause a financial problem for the owner, losing money every second they're not working," Cesar Cerrudo, CTO at IOActive Labs, told ZDNet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Ransomware-Attacke: 4000 Server und 45.000 PCs neu installiert
In zehn Tagen erneuerte Møller-Maersk seine gesamte IT-Infrastruktur. Die Folgekosten von Petya/NotPetya beziffert der Reederei-Konzern mit 250 bis 300 Millionen Dollar. Er strebt jetzt mehr Cybersicherheit als Wettbewerbsvorteil an.
Der Reederei-Konzern Møller-Maersk hat durch die Ransomware Petya/NotPetya einen Schaden zwischen 250 und 300 Millionen Dollar erlitten. Es gelang ihm jedoch, innerhalb von zehn Tagen 4000 Server, 45.000 PCs und 2500 Anwendungen neu zu installieren. Das berichtete auf dem Weltwirtschaftsgipfel in Davos Jim Hagemann Snabe, Chairman von Møller-Maersk.
„Stellen Sie sich ein Unternehmen vor, bei dem alle 15 Minuten ein Schiff mit 10.000 bis 20.000 Containern in einen Hafen einläuft, und Sie haben zehn Tage lang keine IT“, sagte Hagemann. „Man kann sich das fast gar nicht vorstellen.“ Der Maersk-Chef attestierte den Mitarbeitern und Partnern eine „heroische Leistung“ für die schnelle Erneuerung der IT-Infrastruktur. Der dänische Konzern hat Niederlassungen in 130 Ländern und fast 90.000 Mitarbeiter. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE https://www.scoop.it/t/securite-pc-et-internet/?&tag=Costs-of-Cybercirme

|
Scooped by
Gust MEES
|
Ransomware 2017 in numbers | #CyberSecurity #Infographic #Awareness
|



 Your new post is loading...
Your new post is loading...

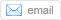








![Stolen California Voter Database Held for Bitcoin Ransom [Updated] | #CyberSecurity #DataBreaches #Ransomware #CryptoCurrency | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/mgyGVgXn_QV_Fs7Qo01leTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)















The threat actors behind the Monti ransomware have resurfaced after a two-month break with a new Linux version of the encryptor in its attacks targeting government and legal sectors.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux