A newly uncovered trojan malware campaign is targeting businesses and higher education in what appears to be an effort to steal usernames, passwords and other private information as well as creating a persistent backdoor onto compromised systems.
Jupyter infostealer has been detailed by cybersecurity company Morphisec who discovered it on the network of an unnamed higher education establishment in the US. It's thought the trojan has been active since May this year.
The attack primarily targets Chromium, Firefox, and Chrome browser data, but also has additional capabilities for opening up a backdoor on compromised systems, allowing attackers to execute PowerShell scripts and commands, as well as the ability to download and execute additional malware.
The Jupyter installer is disguised in a zipped file, often using Microsoft Word icons and file names that look like they need to be urgently opened, pertaining to important documents, travel details or a pay rise.
If the installer is run, it will install legitimate tools in an effort to hide the real purpose of the installation – downloading and running a malicious installer into temporary folders in the background.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Malware



 Your new post is loading...
Your new post is loading...














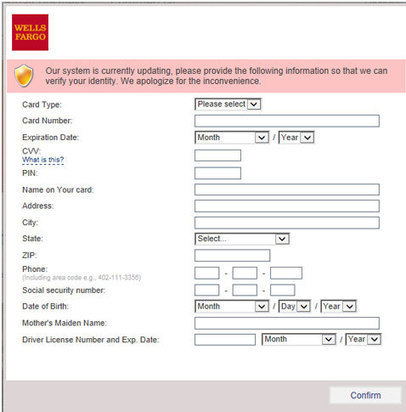



A newly uncovered trojan malware campaign is targeting businesses and higher education in what appears to be an effort to steal usernames, passwords and other private information as well as creating a persistent backdoor onto compromised systems.
Jupyter infostealer has been detailed by cybersecurity company Morphisec who discovered it on the network of an unnamed higher education establishment in the US. It's thought the trojan has been active since May this year.
The attack primarily targets Chromium, Firefox, and Chrome browser data, but also has additional capabilities for opening up a backdoor on compromised systems, allowing attackers to execute PowerShell scripts and commands, as well as the ability to download and execute additional malware.
The Jupyter installer is disguised in a zipped file, often using Microsoft Word icons and file names that look like they need to be urgently opened, pertaining to important documents, travel details or a pay rise.
If the installer is run, it will install legitimate tools in an effort to hide the real purpose of the installation – downloading and running a malicious installer into temporary folders in the background.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Malware